As your organization grows, sharing documentation externally introduces a critical challenge. Your publicly accessible policies, guidelines, and procedures need to reach their intended audiences while maintaining appropriate oversight and control.
Yet many companies struggle with a scattered approach to external sharing that creates unnecessary risk, links distributed across platforms with no central visibility or management. According to Gartner research, 47% of digital workers struggle to find the information needed to effectively perform their jobs – a challenge that extends to managing what information is publicly accessible.
AllyMatter’s Public Link Management system solves this challenge by providing a central command center for all your publicly shared documentation, giving you the oversight and control needed to share with confidence.
The foundation: Why public link management matters
Ineffective management of public links creates significant business challenges:
- When outdated versions of your policies remain accessible after updates
- When you can’t quickly identify which documents are publicly available
- When removing public access requires hunting through multiple systems
- When your team lacks visibility into who created public links and when
For scaling companies, these issues introduce unnecessary risks that can compromise sensitive information or create compliance issues. Effective public link management isn’t just about sharing files; it’s about maintaining complete visibility and control over what your organization makes publicly available.
AllyMatter’s public link management: Core capabilities
Centralized visibility

AllyMatter provides a comprehensive overview of your public documentation:
- Unified public link dashboard showing all accessible documents in one place
- Complete document details including titles and URLs for quick identification
- Creation and modification dates to track when documents were made public
- Ownership information showing who created or last modified each link
- Status indicators that clearly show which links are active
This centralized view eliminates the blind spots of fragmented sharing approaches. Your security team can instantly see exactly which documents are publicly accessible without conducting time-consuming audits across multiple platforms.
Efficient link management
The platform streamlines the oversight of public and private documentation:
- Sorting and filtering options to quickly find specific documents
- Search functionality for locating particular documents by title, URL, or owner
- One-click access to view the actual public documents for quick reference
- Bulk selection capabilities for managing multiple links simultaneously
- Detailed document information available directly within the management interface
These management tools transform what could be an administrative burden into an efficient process. When conducting quarterly security reviews, administrators can quickly assess all public links and make informed decisions about their continued necessity.
Immediate access control
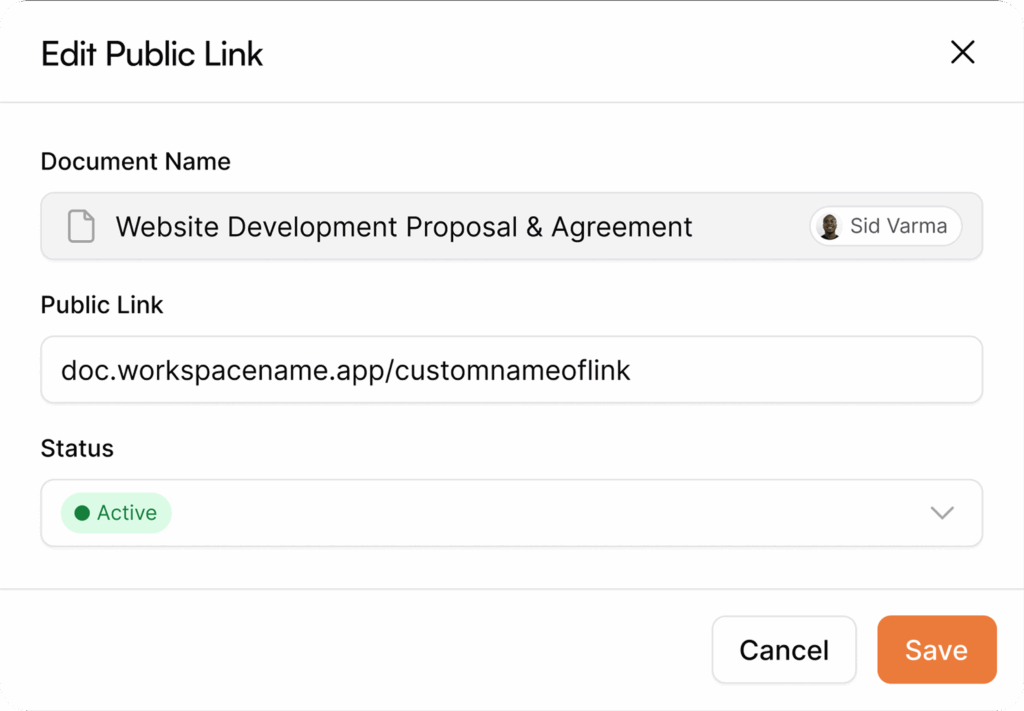
AllyMatter provides direct control over public accessibility:
- One-click revocation for immediately removing public access when needed
- Bulk action support for efficiently managing multiple documents
- Confirmation safeguards to prevent accidental access changes
- Immediate effect ensuring removed links become inaccessible instantly
- Clear visibility of link status changes within the management console
This immediate control eliminates delays in responding to changing sharing requirements. When internal policies change or sensitive information needs to be withdrawn, authorized administrators can immediately revoke public access without dependency on other teams.
For example, Susan, the compliance manager at a growing healthcare company, received an urgent call about a policy document that contained outdated HIPAA guidelines still accessible via public link. Using a centralized interface like AllyMatter’s, she quickly located the document among their 200+ public links, revoked access immediately, and had the corrected version available within minutes – preventing potential compliance issues.
Comprehensive audit trail
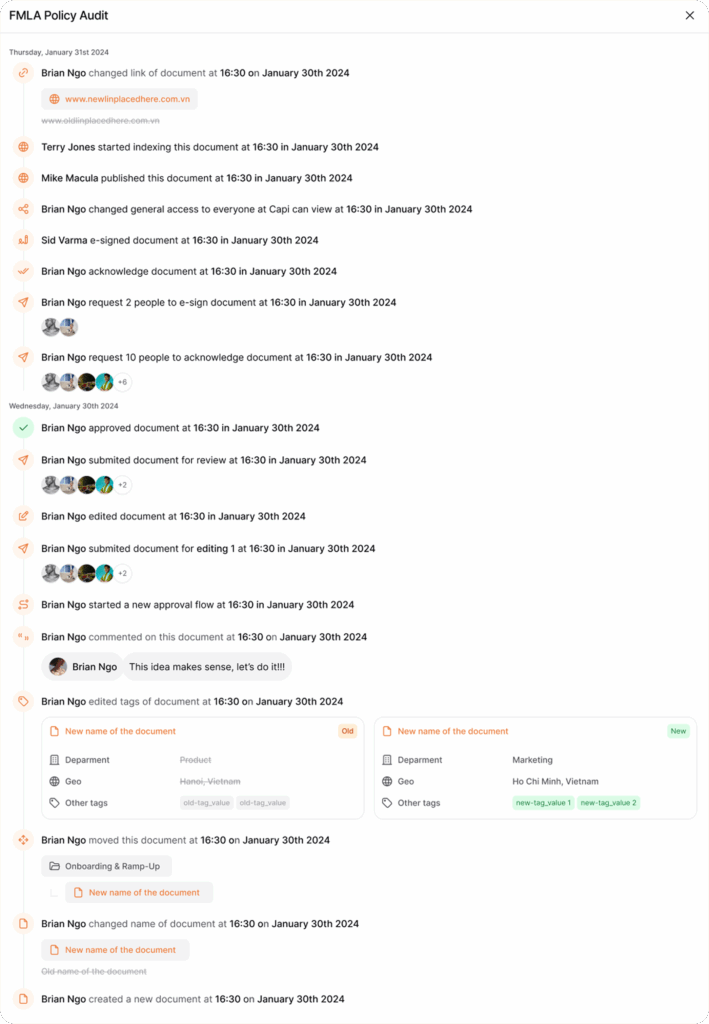
The system maintains complete records of public link management:
- Detailed action logging recording all changes to public link status
- User attribution clearly showing who performed each action
- Timestamps documenting exactly when changes occurred
- Change details capturing the specific modifications made
- Access controls ensuring audit information is available to authorized personnel
This audit capability creates accountability and transparency around public sharing decisions. During compliance reviews or security audits, you can produce complete records showing who made documents public, when they did so, and when access was later modified or revoked.
Real-world public link management scenarios
Security review process
When your security team conducts a quarterly documentation review:
- Administrators access the central Public Link Management interface
- The complete list of publicly accessible documents appears in one view
- Filters help identify outdated materials that may need review
- Documents are sorted by department or owner for systematic evaluation
- Public access is revoked for any documents that no longer need external visibility
- The audit log automatically captures all changes for compliance documentation
This structured approach ensures no public documentation slips through the cracks during security reviews, maintaining tight control over your organization’s public information footprint.
Responding to changing requirements
When a policy needs to be immediately removed from public view:
- Administrators quickly locate the document in the central management interface
- The document’s details confirm it’s the correct target for access changes
- Public access is revoked with a single action
- A confirmation dialog prevents accidental changes
- The document immediately becomes inaccessible to external visitors
- The audit log records who removed access and when
This responsive control enables immediate action when business needs change, eliminating the risks associated with outdated information remaining publicly accessible.
Organizational oversight
When leadership needs visibility into public information sharing:
- Administrators generate a complete view of all publicly accessible documentation
- The list reveals which departments are sharing what information
- Access patterns become visible through creation dates and ownership information
- Any concerning or unauthorized sharing can be immediately addressed
- Regular reviews establish appropriate governance over public information
- The organization maintains control over its external information presence
This oversight capability ensures public sharing aligns with organizational policies and security requirements, preventing uncontrolled information exposure.
Best practices for public link management
To maximize the effectiveness of AllyMatter’s public sharing capabilities:
- Schedule regular public link reviews to ensure continued appropriateness.
- Establish clear ownership for public link management responsibilities.
- Create departmental guidelines for what can and cannot be shared publicly.
- Document rationales for public sharing decisions.
- Implement approval workflows for creating new public links.
By implementing these practices, public sharing becomes a controlled, intentional process rather than an accumulating source of potential security exposure.
The business impact of effective public link management
While managing public links may seem primarily technical, its business impact is substantial:
- Reduced security risk through complete visibility of public information
- Improved compliance with clear documentation of sharing decisions
- Faster response to changing business and security requirements
- Enhanced governance over organizational information
- Greater confidence in your public information posture
For evolving businesses, these benefits translate to stronger security, better compliance, and more effective information governance, essential capabilities as organizations scale and face increasing scrutiny.
Getting started with AllyMatter’s public link management
Implementing effective public link oversight is straightforward with AllyMatter:
- Conduct an initial audit of currently public documentation.
- Consolidate oversight in the centralized management interface.
- Establish review cycles for ongoing management.
- Define clear ownership for public link governance.
- Train administrators on effective usage of the management tools.
With AllyMatter, you can immediately gain control over your public information footprint while developing more sophisticated governance as your organization matures.
Join our waitlist to be among the first to experience centralized public link control.
AllyMatter: Control and confidence in public sharing
In today’s information-rich business environment, sharing documentation publicly isn’t the exception; it’s an everyday necessity. AllyMatter’s Public Link Management transforms this routine function from a potential security blind spot into a controlled, visible process.
Whether you’re conducting security reviews, responding to changing business requirements, or simply maintaining appropriate governance over your organization’s information, AllyMatter’s central management capabilities ensure you always know what’s being shared publicly and can modify access instantly when needed.
Don’t let public sharing become an unmanaged security risk. With AllyMatter, you can confidently share documentation externally while maintaining the control and visibility essential for today’s security-conscious organizations.
Frequently asked questions
How quickly can I revoke public access to a document in AllyMatter?
Public access can be revoked instantly with a single click from the centralized management interface. The change takes effect immediately, making the document inaccessible to external visitors. All revocation actions are automatically logged in the audit trail with timestamps and user attribution for compliance purposes.
Can I see who created public links and when they were made public?
Yes, AllyMatter’s Public Link Management provides complete ownership information and creation timestamps for every public link. The interface shows who created each link, when it was made public, and any subsequent modifications. This transparency is essential for security reviews and maintaining accountability.
Does AllyMatter support bulk management of public links?
Absolutely. The platform includes bulk selection capabilities that allow administrators to manage multiple public links simultaneously. You can filter, sort, and select multiple documents for bulk actions like access revocation, making large-scale management efficient during security reviews or policy changes.
What information is captured in the public link audit trail?
The audit trail records comprehensive details including user attribution (who), timestamps (when), specific actions taken (what), and change details. This includes when links were created, modified, or revoked, providing complete transparency for compliance reviews and security audits.
How does centralized public link management improve security compliance?
Centralized management eliminates security blind spots by providing complete visibility of all publicly accessible documents in one interface. This enables systematic security reviews, immediate response to compliance requirements, and detailed audit trails that demonstrate proper governance over public information sharing.


