As your company grows, managing who can access what becomes increasingly complex. What started as a simple shared drive with “view” or “edit” permissions quickly evolves into a maze of access rights, roles, departments, and security considerations. When your team expands beyond 50 people, basic permission systems no longer suffice. You need structured, scalable user management that grows with your organization.
That’s where AllyMatter’s User Management Console steps in, not just as an administrative tool, but as a strategic platform for maintaining security, transparency, and efficiency across your growing documentation ecosystem.
The foundation: Why user management matters
Poor user administration creates real business challenges:
- When sensitive HR documents accidentally become visible to the entire company
- When departing employees retain access to proprietary information
- When new team members can’t access the resources they need to do their jobs
- When administrators spend hours manually adjusting permissions for each new hire
For rapidly scaling teams, these scenarios represent significant risks and inefficiencies that multiply as your organization expands. Effective user management isn’t just about security; it’s about creating frictionless access to knowledge while maintaining appropriate boundaries.
AllyMatter’s user management console: Core capabilities
1. Role-based access control
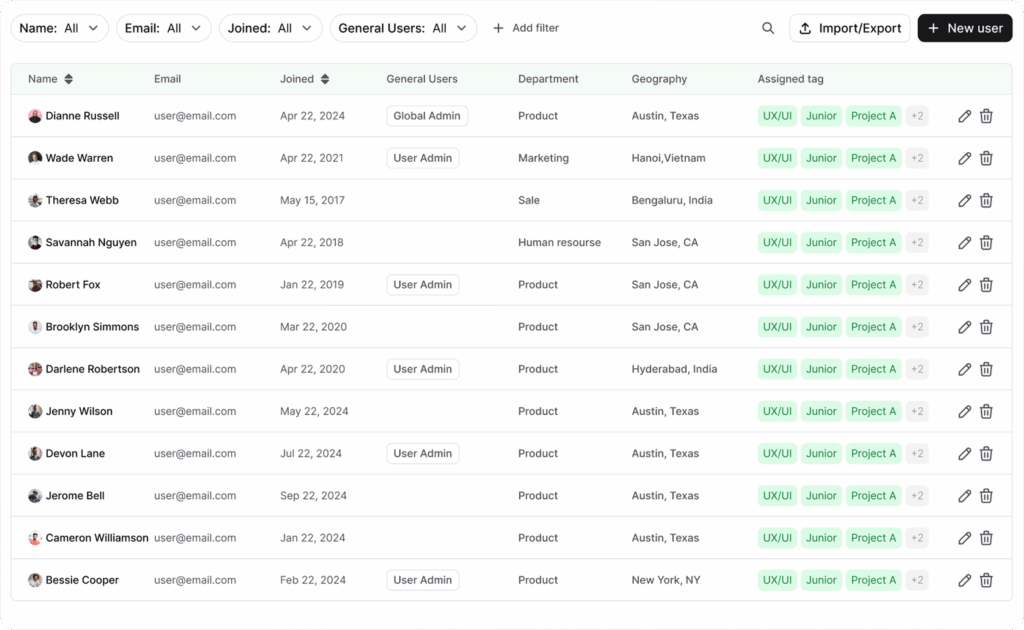
AllyMatter simplifies access management through clearly defined roles:
- Administrators receive complete system control with oversight of all users and content.
- Owners maintain full control over their created documents, including permission management.
- Internal approvers review and approve documents within assigned areas.
- External approvers access only the specific documents requiring their approval.
- Internal editors create and modify content within permitted areas.
- Internal viewers access documents relevant to their department or role.
- Public viewers see only explicitly published public content.
This role hierarchy creates clarity and consistency, eliminating the confusion of custom permission levels for each user. When Finance adds a new team member, you can confidently assign the “Internal Editor” role knowing exactly what they can and cannot access.
2. Integrated tag-based permissions
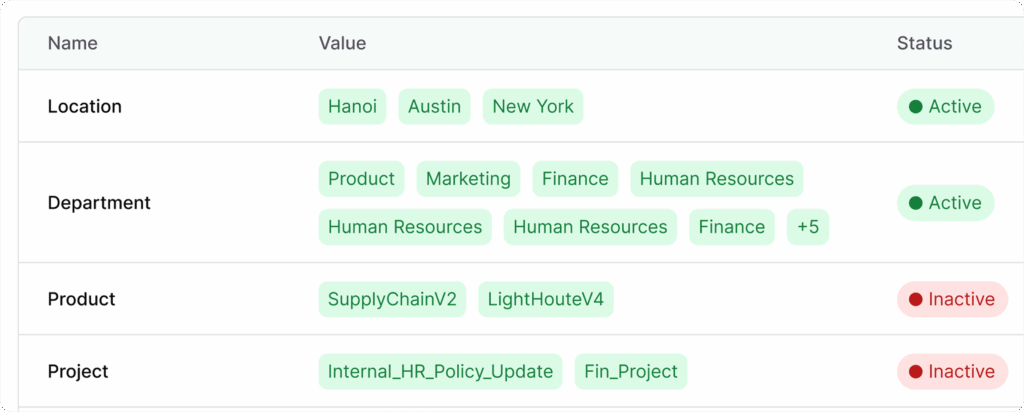
AllyMatter combines roles with a powerful tagging system that precisely controls access:
- Simple tag logic ensures if you have a tag, you can see content with it.
- Department-based tagging ensures information stays within appropriate teams.
- Geographic tagging manages regional access for global organizations.
- Project-specific tagging gives temporary access to cross-functional teams.
- Sensitivity tagging creates additional barriers for confidential information.
Unlike complex matrix-based permission systems, AllyMatter’s tag approach is intuitive and scales effortlessly. When your Legal team needs to share contract templates with Sales, one tag connects the right people to the right resources.
3. Centralized user administration
The console provides a comprehensive command center for user management:
- Unified user directory maintains a complete view of all system users.
- Bulk user operations enable efficient onboarding and role changes.
- User activity monitoring tracks document access and modification.
- Status tracking shows active, inactive, and pending users.
This centralization eliminates the scattered approach of managing users across multiple systems. When your quarterly compliance review requires a complete user access report, you’ll have the information ready in seconds, not days.
4. Automated user lifecycle management
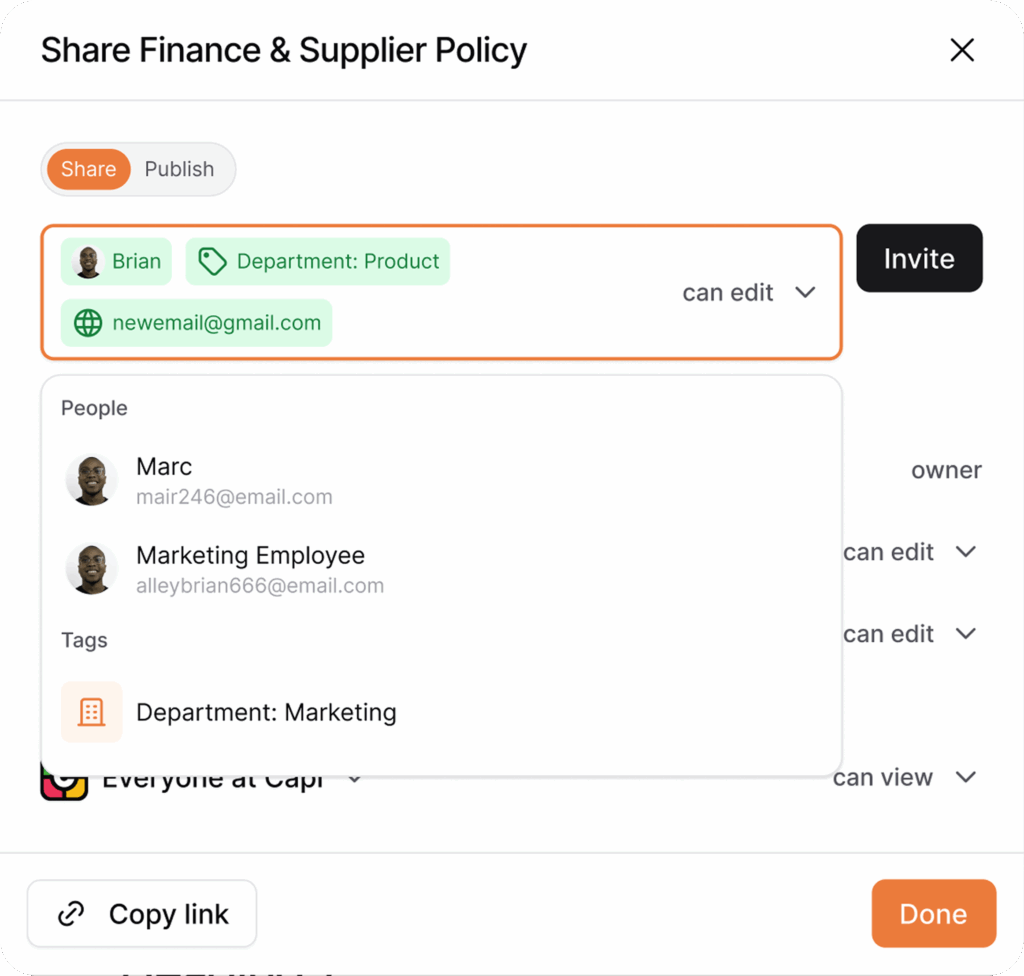
AllyMatter streamlines the entire user journey from onboarding to offboarding:
- Self-service registration with approval workflows for new users
- Automated provisioning based on department and role
- Scheduled access reviews to verify appropriate permissions
- One-click deprovisioning when team members depart
- Access history preservation for compliance and audit purposes
This automation reduces administrative overhead while increasing security. When an employee transfers from Marketing to Product, their access rights update automatically – no tickets, no waiting, no accidental overprivilege.
Real-world user management scenarios
Onboarding new team members
When your HR department welcomes new employees:
- HR initiates the onboarding process through the user management console.
- The system assigns appropriate tags based on department and role.
- New team members instantly gain access to relevant documentation.
- Department-specific onboarding materials become immediately available.
- Training completion is tracked through the same system.
- Managers receive confirmation when onboarding steps are completed.
This streamlined approach ensures new hires have exactly what they need from day one, without overwhelming them with irrelevant information or waiting for manual permission grants.
Managing external collaborators
As your legal team works with outside counsel on contract reviews:
- External users are created with the “External Approver” role.
- Specific documents are shared through secure, time-limited access.
- External activity is logged for compliance purposes.
- Access automatically expires when the project concludes.
- No internal documents are exposed beyond the specific shared items.
- The complete collaboration history remains for future reference.
This controlled approach maintains security while enabling necessary collaboration, eliminating the risks of general access links or email attachments.
Organizational restructuring
When your company reorganizes departments:
- Administrators update the organizational structure in the console.
- User access rights automatically adjust to reflect new reporting relationships.
- Document access changes according to new responsibilities.
- Historical access records preserve the pre-reorganization state.
- Users receive notifications about their updated access rights.
- The system maintains continuity while implementing structural changes.
This adaptability ensures organizational changes don’t create documentation chaos or security gaps, maintaining productivity through transitions.
Best practices for user management
To maximize the effectiveness of AllyMatter’s user management capabilities:
- Design your tag hierarchy thoughtfully before implementing at scale
- Establish clear ownership for user administration within your organization
- Schedule regular access reviews to maintain appropriate permissions
- Document your role assignments to ensure consistent application
- Train administrators on efficient user management workflows
Implement user management if:
- Your team exceeds 50 people
- You handle sensitive information across departments
- External collaborators need document access
- Onboarding takes longer than necessary
- Previous employees still have system access
By embedding these practices into your documentation governance, user management becomes a strategic asset rather than an administrative burden.
The business impact of effective user management
While user administration may seem primarily technical, its business impact is substantial:
- Enhanced security through precise access control and quick offboarding
- Improved compliance with demonstrable access management for audits
- Reduced administrative overhead through automation and self-service
- Faster onboarding getting new team members productive immediately
- Better collaboration through appropriate cross-functional access
These benefits translate directly to operational efficiency, risk reduction, and improved employee experience – critical advantages in competitive markets.
Getting started with AllyMatter’s user management
Implementing effective user administration is straightforward with AllyMatter:
- Map your organizational structure to identify departments and reporting relationships.
- Define your tag hierarchy to reflect your access control requirements.
- Establish user administration workflows for onboarding and offboarding.
- Train key administrators on console operations and best practices.
The beauty of AllyMatter’s approach is that you can start with basic role assignments and gradually implement more sophisticated access controls as your organization matures.
User management as an enabler of growth
In scaling organizations, effective user management isn’t just about controlling access – it’s about enabling the right people to find and use the right information at the right time. AllyMatter’s User Management Console transforms this complex challenge into a streamlined process that supports your growth rather than constraining it.
Whether you’re preparing for rapid team expansion, implementing stricter compliance controls, or simply trying to bring order to permission chaos, AllyMatter’s user management provides the structure and flexibility you need. The result isn’t just better security – it’s a more productive, collaborative organization where information flows appropriately without barriers or leaks.
Don’t let user administration become your growth bottleneck. With AllyMatter, you can turn access management from a friction point into a catalyst for efficient scaling.
Ready to transform your user management approach? Join our waitlist to be among the first to experience AllyMatter’s streamlined access control system.
Frequently asked questions
How does AllyMatter’s role-based access control differ from traditional permission systems?
Unlike complex matrix-based systems, AllyMatter uses intuitive role hierarchies combined with tag-based permissions. This approach eliminates the need for custom permission levels while providing precise control over who accesses what information.
Can external collaborators access our internal documentation through AllyMatter?
No. External users receive the “External Approver” role with access only to specific shared documents. They cannot view internal documentation, and their access automatically expires when projects conclude.
How quickly can new employees gain access to relevant documentation?
New team members receive instant access to department-relevant documentation based on their assigned role and tags. The automated provisioning process eliminates waiting periods for manual permission grants.
What happens to user access when employees change departments?
AllyMatter automatically updates access rights when organizational changes occur. User permissions adjust to reflect new responsibilities while maintaining historical access records for compliance purposes.


