The moment your growing company reaches 50+ team members, a familiar pattern emerges:
- Password reset requests flood your IT inbox.
- New hires spend their first day juggling multiple login credentials.
- Security concerns mount as employees resort to using the same passwords across platforms.
For organizations managing sensitive documentation from financial policies to HR procedures, this creates both productivity bottlenecks and security vulnerabilities. Single sign-on (SSO) solves these challenges by creating one secure gateway to multiple applications, including your knowledge management system.
This article explores how AllyMatter’s SSO integration strengthens security while simplifying access, transforming how growing companies manage their critical knowledge assets.
Why traditional access management fails growing companies
Password-based access to multiple systems creates cascading problems as companies scale. Just consider what happens during a typical onboarding process: new team members receive separate credentials for email, project management tools, CRM, and knowledge repositories. Each system has different password requirements, expiration policies, and security protocols.
This fragmentation leads to predictable challenges:
- IT teams spend valuable time managing account provisioning and password resets.
- Team members experience login fatigue and resort to unsafe password practices.
- Security vulnerabilities increase with each additional set of credentials.
- Offboarding becomes a complex process with lurking security gaps.
For companies managing sensitive documentation, these issues aren’t merely inconvenient; they represent genuine security risks. When IT admins can’t efficiently manage access across multiple systems, critical knowledge assets become vulnerable.
How SSO transforms knowledge base security
SSO integration fundamentally changes how team members access your knowledge base by enabling them to use a single identity provider to authenticate across multiple applications. Instead of remembering separate credentials for each system, users authenticate once through a trusted identity provider.
This approach offers several transformative benefits:
Enhanced security through centralized authentication
With SSO, authentication happens at the identity provider level, not within each application. This means your knowledge base leverages enterprise-grade security standards like multi-factor authentication without requiring separate implementation. For growing companies, this creates institutional-grade security with minimal overhead.
The impact is particularly valuable for sensitive documentation. Finance teams can securely access payment procedure documents, HR managers can maintain confidential employee records, and legal teams can protect regulatory compliance documentation, all through a single authentication point with robust security controls.
Streamlined user management
When new team members join, IT administrators provision access through the identity provider rather than configuring each application separately. Similarly, when someone leaves, revoking access at the identity provider level immediately cuts off access to all connected systems, including your knowledge base.
This centralized approach significantly reduces security gaps during offboarding. For fast-growing startups experiencing regular team changes, this streamlined process ensures former employees don’t retain access to sensitive knowledge assets after departure.
Improved user experience and productivity
Password-related issues consume surprising amounts of productive time. According to research by Yubico and Ponemon Institute, employees spend an average of 12.6 minutes each week dealing with password problems. For a 100-person organization, that represents over 1,000 hours of lost productivity annually.
SSO eliminates these friction points, allowing team members to move seamlessly between applications without repeated login prompts. For knowledge workers who regularly reference documentation across departments, it significantly improves workflow efficiency.
Consider Susan, an HR manager at a scale-up who previously spent 15 minutes each morning logging into separate systems to access employee handbooks, policy documents, and compliance guides. With SSO integration, she now accesses all HR documentation through her single corporate login, transforming those 15 minutes into strategic planning time. For knowledge workers who regularly reference documentation across departments, this frictionless experience significantly improves workflow efficiency.
AllyMatter’s approach to SSO integration
AllyMatter’s SSO implementation takes a comprehensive approach designed specifically for growing companies with evolving security needs.
Flexible identity provider support
AllyMatter’s SSO integration supports multiple identity providers, including:
- Microsoft Azure AD
- Google Workspace
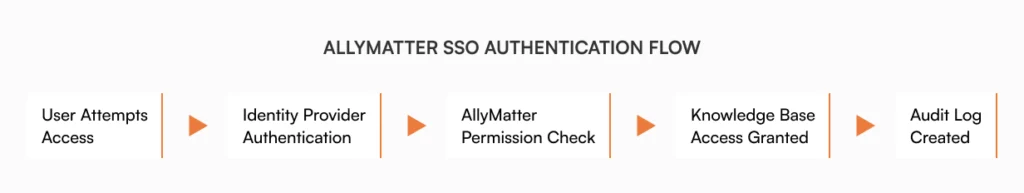
This flexibility allows companies to maintain their existing identity infrastructure while extending secure authentication to their knowledge management system. For organizations already using Google Workspace or Microsoft environments, implementation requires minimal additional configuration.
Granular access controls with SSO
While SSO provides the authentication layer, AllyMatter enhances this with nuanced authorization capabilities. Once authenticated, users receive access only to documentation relevant to their role, department, or project, providing the perfect balance between accessibility and security.
This combination addresses a common concern with SSO: that simplifying access might compromise security by creating an “all or nothing” permission model. AllyMatter’s approach ensures that while authentication is streamlined, authorization remains precisely controlled.
For example, when a marketing team member authenticates through SSO, they gain immediate access to marketing materials while engineering documentation remains protected, all through a single sign-on experience.
User provisioning and deprovisioning
AllyMatter supports SCIM (System for Cross-domain Identity Management) for automated user provisioning and deprovisioning when integrated with compatible identity providers. This capability streamlines user lifecycle management by automatically:
- Creating user accounts in AllyMatter when added to the identity provider
- Updating user attributes and group memberships when changes occur
- Deactivating accounts when users are removed from the identity provider
For IT administrators managing growing teams, this automation significantly reduces manual configuration while strengthening security by eliminating provisioning delays and deprovisioning oversights.
Implementing SSO for your knowledge base: Practical steps
Implementing SSO for your knowledge management system follows a systematic approach:
Consider SSO implementation if:
- Your organization has 50+ team members managing multiple credentials
- IT spends significant time on password resets and account provisioning
- Security policies require centralized authentication controls
- Team members frequently access documentation across departments
Assess your current identity infrastructure
Before implementation, audit your existing identity management approach:
- Which identity provider does your organization currently use?
- What authentication protocols are supported (SAML, OAuth, etc.)?
- How are user attributes and groups currently structured?
This assessment ensures your knowledge base SSO implementation aligns with existing systems rather than creating parallel authentication processes.
Configure your identity provider
The specific configuration varies by provider, but generally involves:
- Registering AllyMatter as a service provider in your identity system
- Configuring attribute mapping to transfer user information
- Setting authentication policies (MFA requirements, session duration)
- Testing the authentication flow with sample users
Follow this decision path: If your company uses Google Workspace, then configure SAML 2.0 integration. If using Microsoft Azure AD, then implement OAuth protocols with SCIM provisioning.
AllyMatter’s implementation guides provide step-by-step instructions for each major identity provider, simplifying this technical process.
Manage the transition
Transitioning to SSO requires thoughtful change management:
- Communicate the upcoming change to team members with clear instructions.
- Provide a transition period where both authentication methods work.
- Offer support channels for users experiencing difficulties.
- Gather feedback to address any workflow disruptions.
This phased approach ensures team members adapt smoothly without losing access to critical documentation during the transition.
Practical SSO implementation scenarios
Let’s explore how different teams might leverage SSO integration with their knowledge management platform:
IT administration scenario: An IT administrator at a growing fintech company needs to onboard 20 new employees across multiple departments. With AllyMatter’s SSO integration, the admin configures access once in the identity provider, automatically granting appropriate knowledge base access based on department groupings. This eliminates manual configuration across multiple systems and ensures new hires have immediate access to relevant documentation.
HR documentation scenario: A human resources team stores sensitive employee policy documents in their knowledge base. With SSO integration, HR professionals access these documents through their existing credentials with additional security factors already configured in their identity provider. This seamless authentication process maintains security without creating friction when HR needs to quickly reference specific policies.
Cross-functional project scenario: A product development initiative involves team members from engineering, marketing, and customer support. SSO integration allows these team members to seamlessly access centralized project documentation without managing separate credentials, while department-specific tags ensure each user only sees appropriate documentation for their role.
Transform knowledge base security with AllyMatter’s SSO solution
Implementing SSO for your knowledge management system transforms how your organization balances security and accessibility. By centralizing authentication while maintaining granular authorization, companies create an environment where team members can efficiently access the information they need without compromising security standards.
For growing companies managing increasingly complex documentation needs, this approach provides enterprise-grade security without enterprise-level complexity. The right SSO implementation ensures that as your knowledge base expands, your security posture strengthens rather than fragments.
AllyMatter’s SSO integration ensures that as your knowledge base expands, your security posture strengthens rather than fragments. By connecting your identity provider to our platform, you create a seamless experience where knowledge flows securely to those who need it, when they need it.
Want to learn how AllyMatter’s SSO integration can strengthen your knowledge management security? Join the waitlist.
Frequently asked questions about SSO integration
How long does AllyMatter’s SSO implementation typically take?
While SSO does require initial configuration, most organizations complete implementation within a few days, not weeks. For companies already using a major identity provider like Azure AD or Google Workspace, the process is particularly straightforward.
How does SSO impact knowledge base performance?
SSO typically improves performance by eliminating authentication delays within the knowledge base itself. Since authentication happens at the identity provider level, knowledge base access becomes more responsive once authenticated.
Can we still use password-based authentication for some users?
Yes, most implementations support hybrid authentication methods during transition periods. This flexibility is particularly valuable for external collaborators who may not be in your identity provider system.
What happens if our identity provider experiences downtime?
While rare, identity provider outages can temporarily impact access. Some SSO implementations offer session persistence that allows continued access during brief outages if users have recently authenticated.
Does SSO help with compliance requirements?
Absolutely. SSO provides centralized authentication logs, consistent security controls, and streamlined access revocation, all valuable capabilities for meeting compliance standards like SOC 2, HIPAA, and GDPR.
How does AllyMatter’s SSO compare to building custom authentication?
AllyMatter’s pre-built SSO integration reduces implementation time from months to days. Our solution includes automated user provisioning, role mapping, and compliance logging that custom solutions require significant development resources to achieve.


